No matter where your company is located and in which field it operates, one thing is always true: today, SOC 2 is one of the standards tech companies should meet to be recognized for their security practices.
If you’re tackling an audit for the first time, it can feel like you don’t even know where to start. And let’s be honest, hiring expensive security consultants isn’t always an option, especially if cash is tight. That’s exactly why I’m writing this — a practical guide with just enough theory to get you through it.
I’m going to assume you’ll be using some tooling. Based on my experience, modern tools are incredibly helpful and worth every penny. Trying to obtain certification without them is often a headache you don’t need, and it’ll cost you more time and money in the long run.
Minimal Theoretical Background
SOC 2 comes in two options:
- Type 1. This is a one-time certification that says your systems were compliant at a specific point in time.
- Type 2. This is more intense — it requires continuous compliance over a set timeframe (called the observation period) and proves that your systems stayed compliant throughout.
Type 2 is tougher to get, but it’s also more trustworthy. If you want people to take your security seriously, this is the one that you usually aim for.
In this guide, I’m focusing on Type 2 as the process for Type 1 is almost the same, just without the observation period.
Another thing to know is that SOC 2 is all about security controls backed by evidence and gathering it will be your big task.
This timeline will help you understand the overall process:
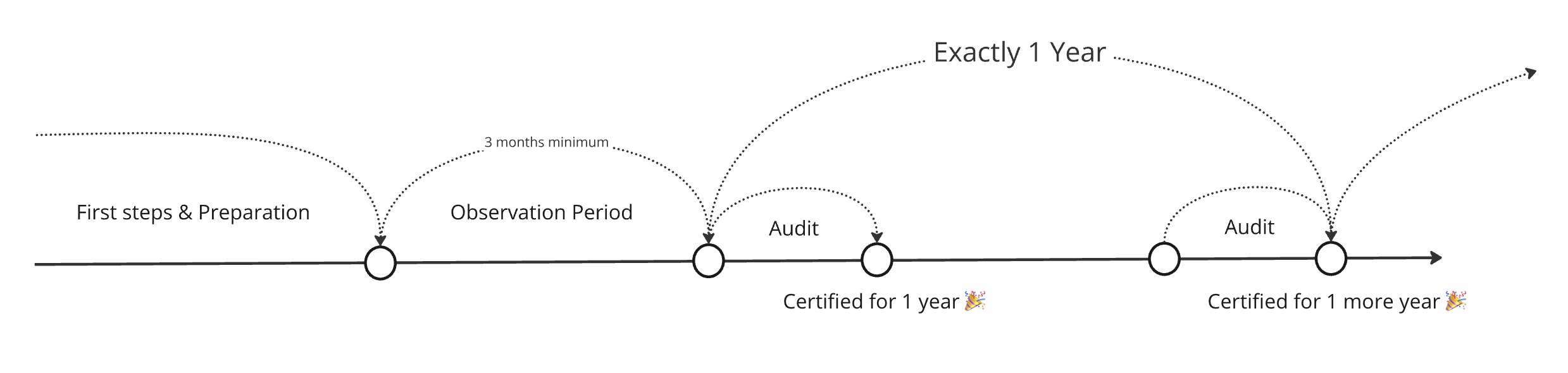
Let’s take a closer look.
First Steps and Preparation
At this step, you’ll handle the majority of the heavy lifting, so it’s important to approach it right, here you will have to understand the current state of your system and make it secure, reliable, and private:
1. Choose a Service to Gather Your Evidence
Remember when I said gathering evidence is one of the biggest challenges? Well, good news: there are plenty of platforms out there designed to collect and store evidence for you.
Why Use a Platform?
- They save a ton of time.
- Many of these platforms partner with auditors, making it easier (and cheaper) to get certified.
- They include templates and automation that make the whole process feel way less overwhelming.
Cost: For companies of approximately 50 people, the annual cost of SOC 2 certification is typically around $4,000–$5,000, depending on the provider and scope.
Examples: Vanta, Drata, Secureframe, Sprinto, and many more.
How Do You Choose the Right One?
Look for automation. You’ll want something that integrates with your tools — project management systems, messaging platforms, cloud services, version control, and so on. The more automation it offers, the less manual work you’ll need to do.
Can You Do It Without a Platform?
Yes, it’s possible, but in my experience, it’s not the best approach, and here’s why:
- These platforms save you so much time, it’s not even funny — especially if your team is small.
- Auditors love these tools because they make their jobs easier. This can mean much cheaper and faster audits and fewer headaches for you.
2. Understand the Weaknesses in Your Systems
Once you have a security platform, it’s time to connect all your systems to it, run checks, and understand where you are right now.
Here’s what you typically see after everything is configured:
- Less-prepared companies might start with around 60% readiness. It usually takes 2–3 months to close the gaps.
- Average companies are around 80% ready, with gaps that can be fixed in a month.
- Well-prepared organizations can hit 85–90% readiness, needing only a couple of weeks of work.
3. Address Main Security Gaps
Addressing vulnerabilities is a key step in preparing for SOC 2 certification. Instead of trying to tackle everything at once, focus on impactful measures that help you resolve the most issues with the least effort.
Role-Based Access Control
Role-based access control ensures that users and systems only get the permissions they actually need to perform their tasks. Start with a thorough audit of user permissions to identify and remove unnecessary access. Replace shared accounts with individual accounts tied to specific roles, and schedule regular reviews to keep permissions aligned with current responsibilities. Adopting the principle of least privilege reduces the risk of unauthorized actions and provides better oversight of your systems.
Identity Providers and Centralized Access Control
After mapping out user groups and roles, the next logical step is setting up an Identity Provider (IdP). Centralizing access control with an IdP such as Okta, MS Entra, or Google Workspace allows you to manage authentication and permissions in one place. This simplifies granting and revoking access, helps maintain proper permissions, and provides audit logs to meet compliance requirements.
Start by identifying your critical systems and integrating them with your chosen IdP. Enable single sign-on (SSO) and multi-factor authentication (MFA) to enhance security. Once centralized, enforce group-based access policies aligned with roles, ensuring sensitive environments are only accessible to authorized personnel.
While cloud services often charge extra for SSO, the investment quickly pays off by improving security and saving engineers time on access management.
Infrastructure as Code
Standardizing infrastructure with Infrastructure as Code (IaC) tools like Terraform improves consistency, reduces manual errors, and enforces security best practices. Document your infrastructure and create configurations that work across development, staging, and production environments.
IaC not only strengthens security and simplifies audits but also significantly boosts the flexibility and maintainability of your infrastructure by providing a clear, version-controlled record of changes.
Securing CI/CD Pipelines
CI/CD pipelines are essential for modern software delivery, but without proper security, they can also become a source of vulnerabilities. Enforce mandatory code reviews and integrate tools to automatically scan for vulnerabilities in dependencies and configurations. Restrict access to deployment tools so that only trusted individuals can approve changes to production. This ensures every change is thoroughly reviewed, minimizing the risk of insecure code being deployed and maintaining the integrity of your software.
Security Awareness Training
Help your team recognize and respond to security threats by running regular training sessions or simulations. These can improve awareness of phishing attempts, secure data handling, and other common risks. Establish a straightforward process for reporting suspicious activity, so employees feel confident acting as a first line of defense. A well-trained team significantly reduces the likelihood of human error leading to security incidents.
Establish Issue Mitigation Policies
Having clear processes and accountability is crucial for effectively addressing vulnerabilities. Assign specific responsibilities for compliance areas or security issues to individuals or teams, and track progress using task management tools. Set deadlines for resolving issues and review progress during regular meetings. This structured approach keeps priorities aligned and ensures consistent progress toward compliance.
Observation Period
Once you’ve closed all the critical security gaps, you’ll enter what’s called the observation period — a time frame during which your evidence is continuously gathered, cataloged, and stored.
For your first audit, this period usually lasts at least three months, as per the standard. After successfully completing it, you’ll receive a certification valid for one year. To keep your certification active, you’ll need to repeat the process at least annually. In essence, this means you’ll be in a permanent observation period, as there should be no gaps after your first certification.
Some key points to remember:
- Everything you collect during the observation period will be shared with your auditor.
- No security checks should fail, and no issues should remain unaddressed.
During this time, treat your company as if it’s already fully SOC 2 compliant. This approach will not only help you meet the standard but also build habits that make future audits much easier.
The Audit and Certification
Congratulations on completing the observation period! What’s next?
To get certified, you’ll need to be audited by an external, independent, certified organization. Here’s something important to know about these companies:
- Audit costs can range from $2,000–$3,000 to $30,000–$40,000, depending on the auditor, your size, the complexity of your system, and the tools you use to gather evidence.
- A higher cost doesn’t necessarily mean the company is a good fit. Meet with at least 3–4 auditors to find the one that works best for you.
- An easy way is to ask your security platform provider for introductions. They usually have a range of recommended auditors who are already equipped to work with their platform.
As searching for the right company can take a while, it’s important to start looking at least one month before your observation period ends.
Once you’ve found an auditor and are ready to start the audit, here’s what happens next:
- You’ll officially kick off the audit, and your auditor will get access to every piece of evidence you have collected during your observation period.
- The auditors will review your evidence. This can take anywhere from 1 to 4 weeks, depending on your system, auditor, and platform.
- Assuming all security checks pass at the start of your audit, there are two possible outcomes:
- Everything checks out — congratulations! A few formalities, and you’re certified.
- There are questions or failed controls. Fix the issues or explain why they’re acceptable, and you can still get certified if your explanation is solid.
What’s Next?
SOC 2 Type 2 isn’t a one-time deal. To keep your certification active, you’ll need to pass annual audits from now on. Now that your system is in great shape, you need to keep it that way and maintain the highest security standards required by SOC 2.
Once you’ve gone through it the first time, you’ll have a pretty good idea of what to do. Future audits will be much easier. Just keep improving your system, and you’ll be golden.









